Slider
Uninstalling an application doesn’t erase the evidence that it was ever used
Did you know that uninstalling an application doesn’t erase the evidence that it was ever used? Windows maintains a hidden record for programs you run to improve startup performance. This mechanism is called Prefetch . Stored in C:\Windows\Prefetch , these . pf files record details such as: The exact date and time the program was executed The file path it was launche…
Read moreMy first (intentional) self-infection
Back in 2004, Sasser, one of the most "famous" computer worms ever made was creating havoc through to world of Windows based PC's. During the summer of that year, I was based (although temporarily) in my home-town Bucharest. Just started studying for the CCNA exam that I've planned to take at the end of July. Incoming long nights, studying, playing …
Read moreHow to install the latest video card drivers in Linux Mint
Ok, since I moved to Linux Mint, after completing the installation and the update + upgrade stuff, my video card was still making shitload of noise. In order to calm it down, you need the latest drivers. Below is a short tutorial on how to install the latest drivers for your (nVidia) video card in Linux Mint. Open the terminal and type: ubuntu-drivers devices This wa…
Read moreHow to fix "An installation step failed - Kali Linux 2020" in VirtualBox installation
Even though I switched to Ubuntu a while ago, I decided to expand my home-lab and also add Kali Linux into VirtualBox. The installation process went smooth, up to one point, and then boom. Fuc*** error pop-up: "An installation step failed. You can try to run the failing item again from the menu, or skip it and choose something else. The failing step is: select a…
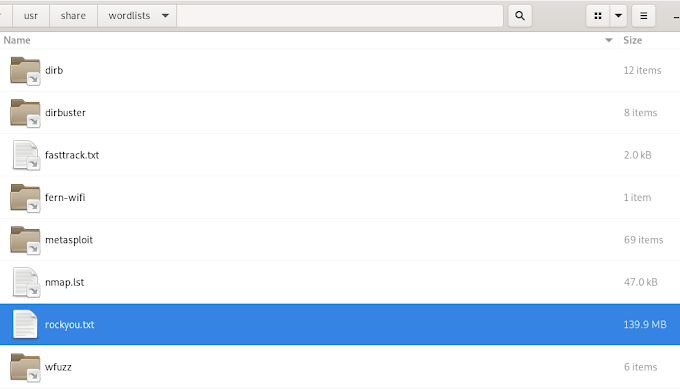
Read moreHow to locate and extract the "RockYou" wordlist in Kali Linux
RockYou is one of the most popular wordlists that contains common used passwords. The history of rockyou was best explained in the Darknet Diaries episode 33. This is a great podcast and you can listen to it the episode here . As mentioned in the episode, the list is part of the default Kali Linux installation. Then again, it's archived and you have to extract it…
Read moreHow to install Tor in Kali Linux 2020 and fix "run Tor as root" error
In order to install Tor Browser on your Kali Linux, open your terminal and type: apt update Once this is complete, run * : apt-get install tor torbrowser-launcher Now, try and open Tor, either form the terminal of from your Applications menu: torbrowser-launcher In case you'll get the same error I got, “The Tor Browser Bundle should not be run as root. Exiting”,…
Read moreYour first basic Kali Linux commands - you should actually know
Back in the years when I started messing around with Linux distro's, my first choices were Mandriva, Suse and Ubuntu. Since then, Mandriva became Mandrake. Otherwise, the rest of the distributions I used to work on, kept their names - btw, I loved Suse and Ubuntu. In the office, we managed to find out the admin passwords and we were able to install games on our o…
Read moreUpdate and upgrade your Kali Linux installation with a script - second version
Howdy, pirates! In my previous (very old) tutorial , I tried to show you how to create a script that will automatically update and upgrade your Kali Linux installation. Since this post is from 2015, you might guess it's actually not working with the current version of Kali. So, I had to figure out something else. In case you're lazy enough to click on the lin…
Read moreHow to Install Nessus in Kali Linux
Nessus is a proprietary vulnerability scanner developed by Tenable, Inc. For more information you can visit their website here . Nessus should be a must-have for any penetration tester. Below are the steps on how to install Nessus in Kali Linux. Download the latest version from here - look for the Debian version (amd64.deb). At the time of writing this tutorial, the …
Read moreHow to install a torrent client on Kali Linux
Personally, I'm a big fan of μTorrent on Windows but, since I switched from Windows to Linux, I struggled to find a good torrent client. Mostly on Kali Linux, it used to be a pain in the a**. Enter, qBittorrent. Even though, on the whole market, it's just on the 6th place on the torrent clients market, for me, on Kali Linux, it does the job. Ok, enough "…
Read moreHow to increase the sound volume above 100% in Kali Linux
I have an older laptop, 15" display, good sound volume in Windows 10, but whenever I boot into Kali, the sound wasn't that good. So, how can you increase the sound volume above 100% in Kali Linux? Follow the tutorial below and you're good to go. Once in Kali Linux, open your console and type the code below: sudo apt-get install pulseaudio pavucontrol …
Read moreMy first computer
You'll see this in many books, movies, documentaries, etc. What was your first computer and how you got into InfoSec and/or IT? I was an anti-tech person. I used to make comics, paint and spend most of my time playing acoustic/classical guitar. I was into classical music & books. Then, in the autumn of 2003, I got my first computer: a Pentium 1, 600 Mhz, wi…
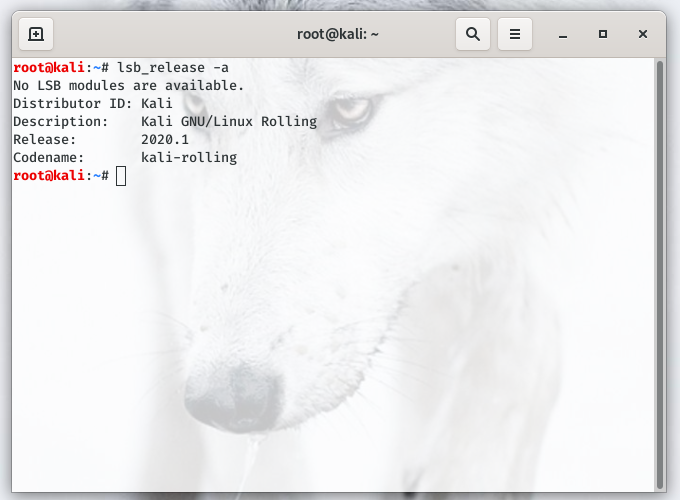
Read moreHow to check your current version of Kali Linux - or any other Linux system
Since Kali Linux rolled out their newest version (as of last night/yesterday - yeah, local time is a bitch), many people wondered if they're using the latest version (or not!) of the operating system. Since the Kali Version I use is a "rolling" version, this means that if you update & upgrade, you're good to go. What is a "rolling" ve…
Read moreHow to edit Kali Linux Repositories/Sources (apt sources.list) using Gedit or Leafpad
How many times have you messed-up your Kali Linux repositories/sources list? How many times you forgot how to edit the list using a text editor (available in Kali Linux)? It happened a lot of times to me so, I'll just keep this as a note for myself. My repositories list contains only two lines of text. In case you've changed it and need to get it back to the…
Read moreThere are no secrets better kept than the secrets everybody guesses
Below is the updated list of websites which have been informed about their security flaws - per email, social media profiles, etc. At the time of this post, the list contained 237 websites. No user data has been compromised and the security flaws were ethically disclosed. The list will be updated on a monthly basis. 7thsensedesign.com addcar.ro aeonevents.co.uk af…
Read moreVisits
Popular Posts
-
RockYou is one of the most popular wordlists that contains common used passwords. The history of rockyou was best explained in the Darknet D...
-
Blogger has the option to set a custom page not found message and redirect (if needed). For my personal blog I decided not to only add a ...
-
Personally, I'm a big fan of μTorrent on Windows but, since I switched from Windows to Linux, I struggled to find a good torrent client....
-
How many times have you messed-up your Kali Linux repositories/sources list? How many times you forgot how to edit the list using a text edi...
-
Creating scripts is easy in Linux distributions, you just need access to any text editor - Linux has plenty available (gedit or gvim, to nam...
-
In order to install Tor Browser on your Kali Linux, open your terminal and type: apt update Once this is complete, run * : apt-get install ...
-
Even though I switched to Ubuntu a while ago, I decided to expand my home-lab and also add Kali Linux into VirtualBox. The installation proc...
-
During the " Reconnaissance " phase we might need to frequently access the targeted website and this can trigger some alarms. I us...
-
You'll see this in many books, movies, documentaries, etc. What was your first computer and how you got into InfoSec and/or IT? I was ...
-
I have an older laptop, 15" display, good sound volume in Windows 10, but whenever I boot into Kali, the sound wasn't that good. So...
Popular Posts
How to check your current version of Kali Linux - or any other Linux system